VPC
Select the Your VPCs link to the left side of the VPC Dashboard.
In the VPC console, create a new VPC. You can use your own configuration or copy the one in the screenshot below.
Take a note of the VPC id when you create the VPC.
Subnets
After creating a VPC you will need to create a private subnet for the dashboard application and two public subnets for the load balancer.
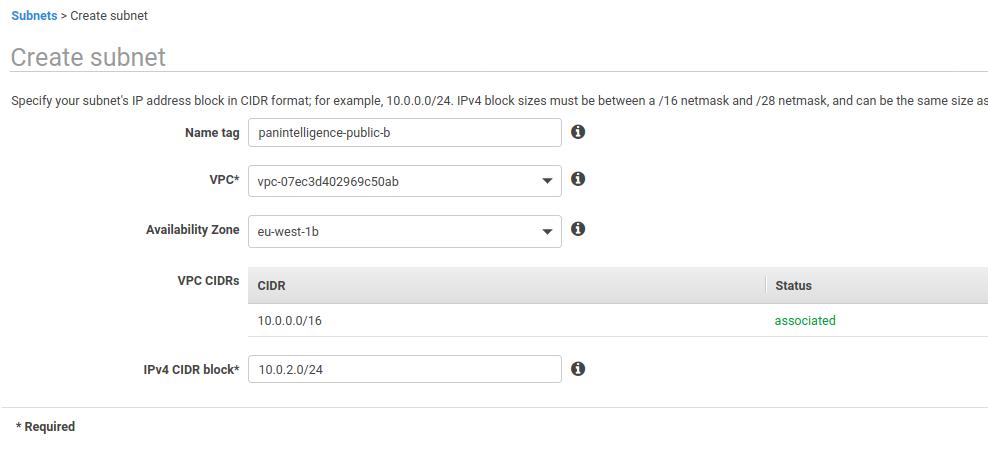
In the subnet section of the VPC service, create a subnet.
You can choose your own Name tag, Availability Zone and IPv4 CIDR block if you know what to set. Our recommendations are shown in the screenshot below. Take a note of the subnet id of the created subnet.
Next, create two more subnets using the configuration in the two screenshots below.
You can choose your own configuration for Name tag, Availability Zone and IPv4 CIDR block, but make sure the availability zones and IPv4 CIDR blocks are different.
Internet Gateway (IGW)
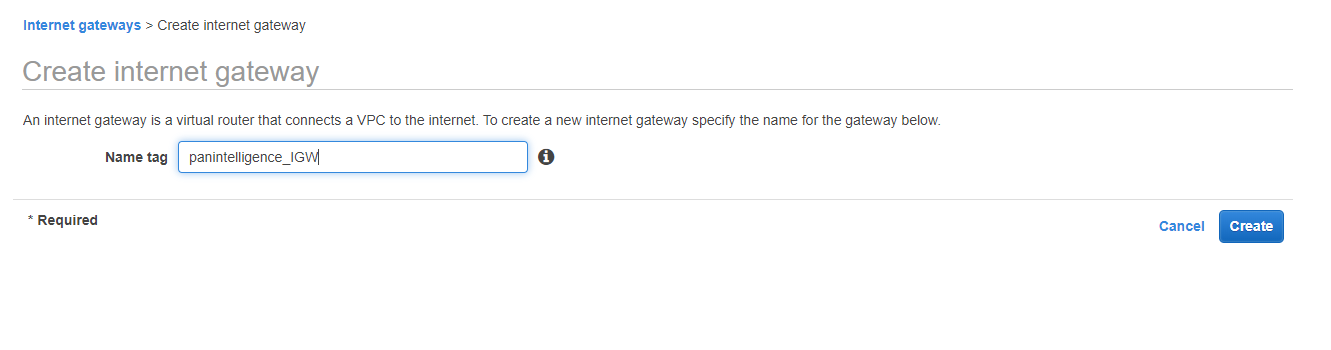
To the left of the VPC dashboard select Internet Gateways and create an IGW.
You will need to create an IGW to route traffic from the VPC to the internet.
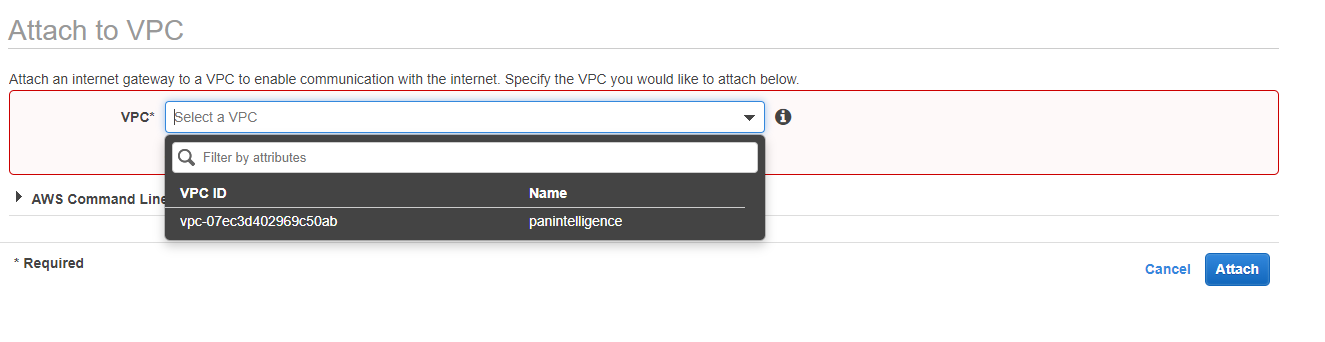
You then need to attach the IGW to the VPC. To do this, select the IGW you just made, select the Actions dropdown and select Attach to VPC from the dropdown. Select the VPC you created earlier.
Route Tables
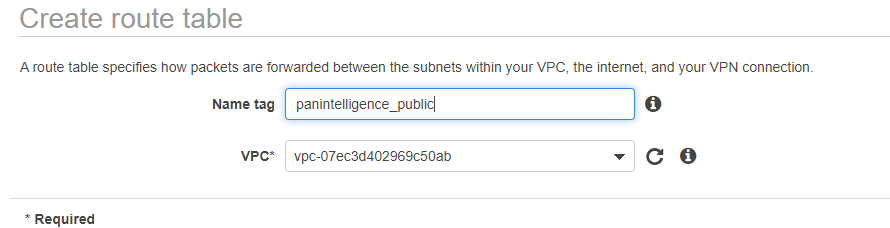
To the left of the VPC dashboard select Route Tables and create a route table.
You need to create a route table to route traffic from your public subnets to the IGW.
Give the VPC a name and select the VPC you created earlier.
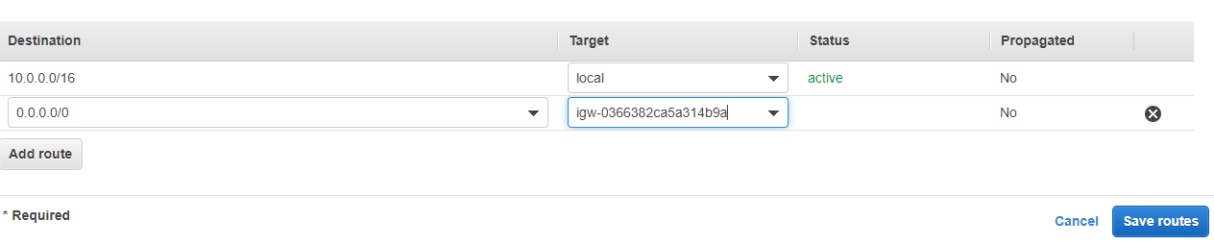
You then need to configure the route table to direct all traffic to the IGW.
To do this, select the route table and select the Routes tab at the bottom. Then select Edit routes. Configure the route to be the same as the screenshot below. For the target select the IGW you created.
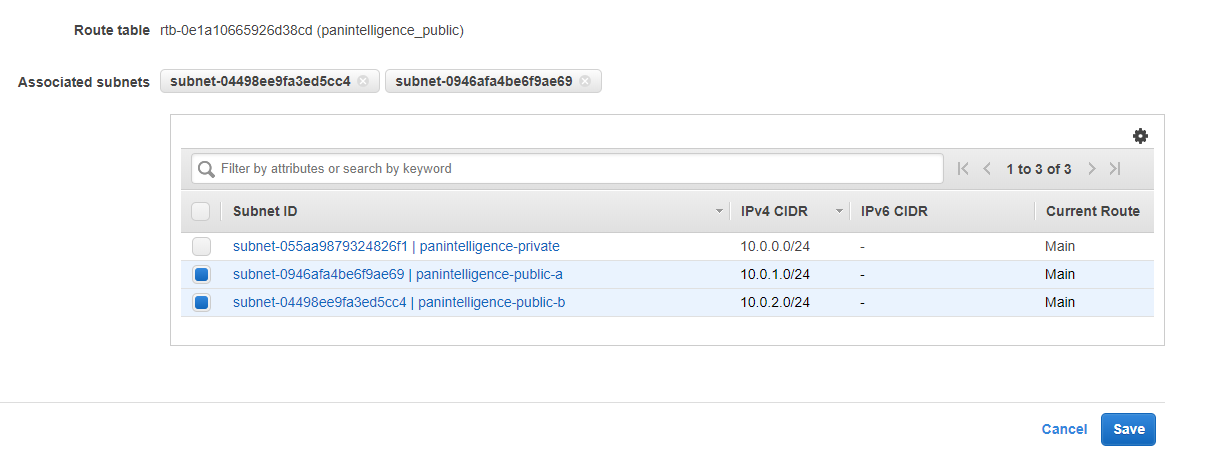
After editing the routes, select the Subnet Associations tab at the bottom and select Edit subnet associations.
Select the two public subnets you created earlier, as shown in the screenshot below. Make sure you select the public subnets and not the private subnet.
The private subnet will automatically use the default route table which does not have access to the internet.
Network Access Control List (NACL)
To the left of the VPC dashboard select Network ACLs and create a network ACL.
We suggest creating NACLs to add an additional layer of security to your stack.
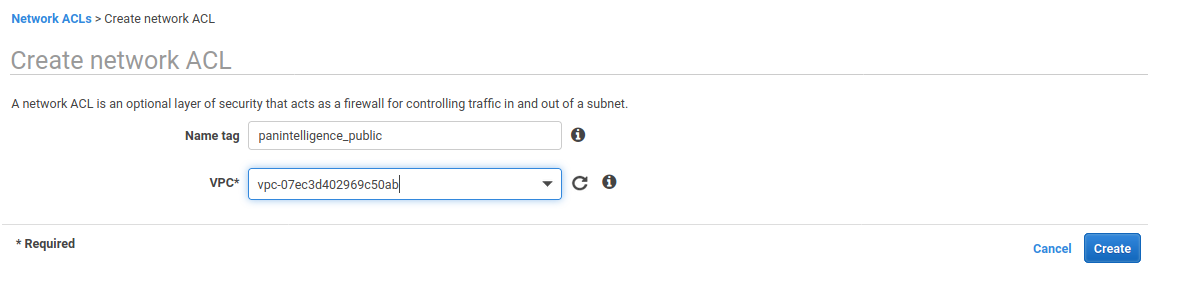
We need to create a NACL for the public subnets.
Create a NACL, using the configuration in the screenshot below. Make sure to set the VPC to the one you created earlier.
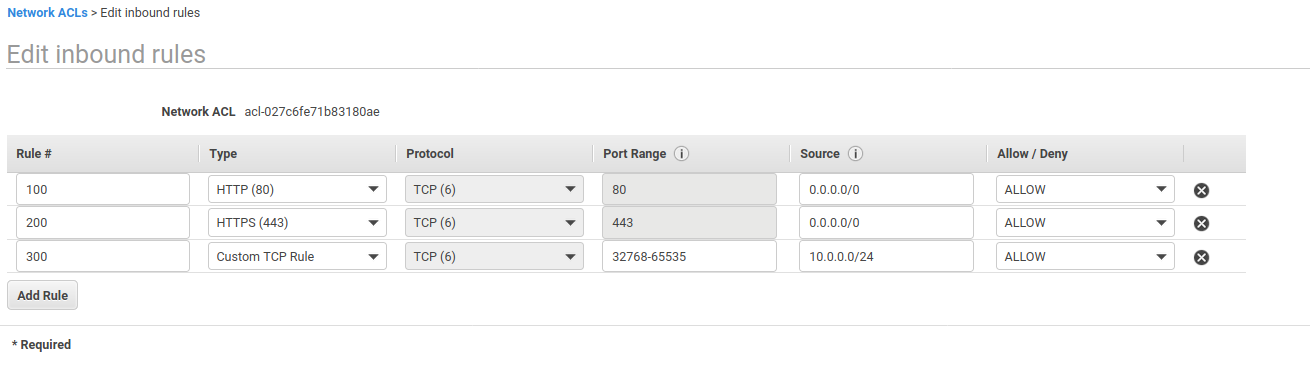
Select the NACL you just created. Select the Inbound Rules tab. Edit the inbound rules and configure it like the screenshot below.
Make sure you replace the CIDR block with the private subnet CIDR block if you changed it when creating the subnets.
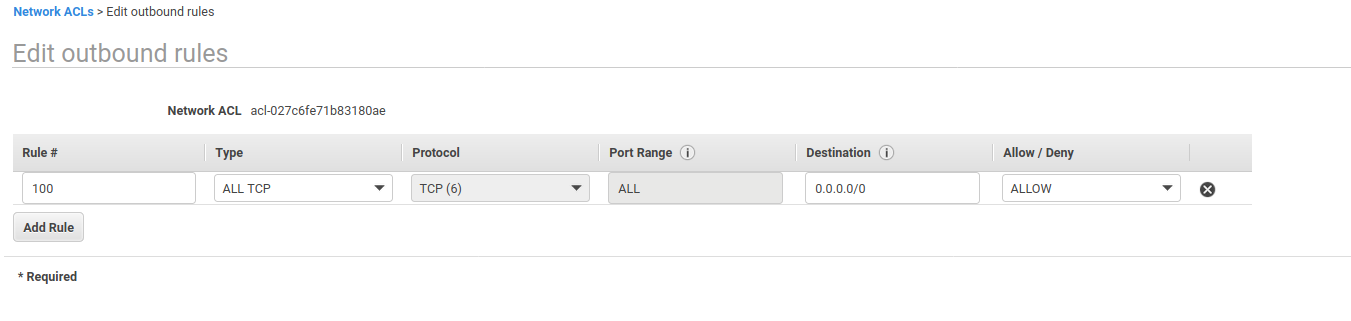
After saving the inbound rules, select the Outbound Rules tab and edit the outbound rules.
Configure the outbound rules to be the same as the screenshot below.
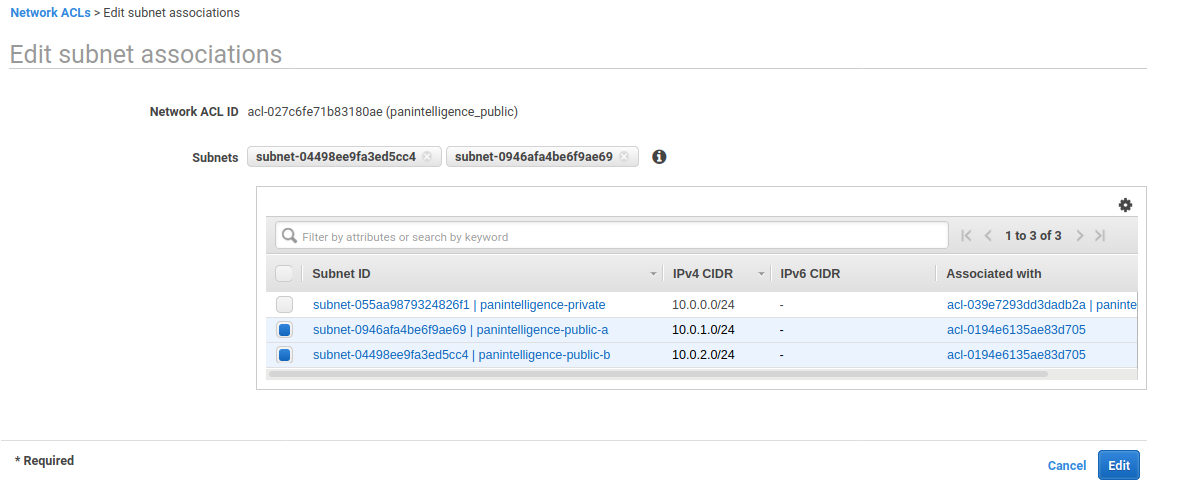
After saving the outbound rules, select the Subnet associations tab at the bottom and select Edit subnet associations.
Select the public subnets you created and click Edit.
Security Groups
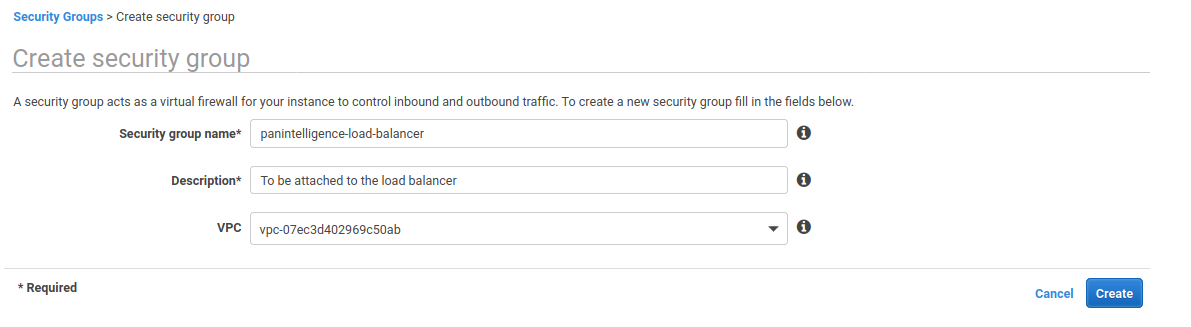
To the left of the VPC dashboard select Security Groups and create a security group.
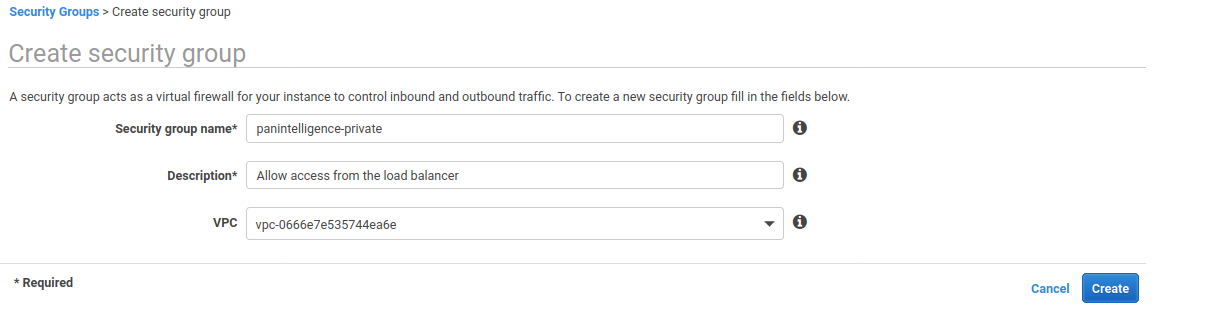
We need to create a security group for the load balancer and a security group for the dashboard application.
Configure the new security group using the image below.
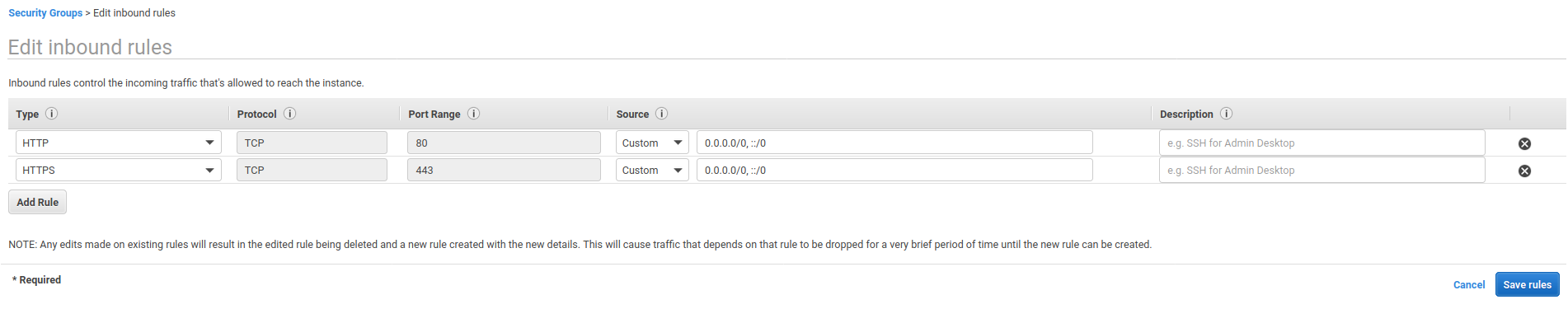
Select the created security group and select the Inbound Rules tab. Edit the inbound rules and configure it to match the screenshot below.
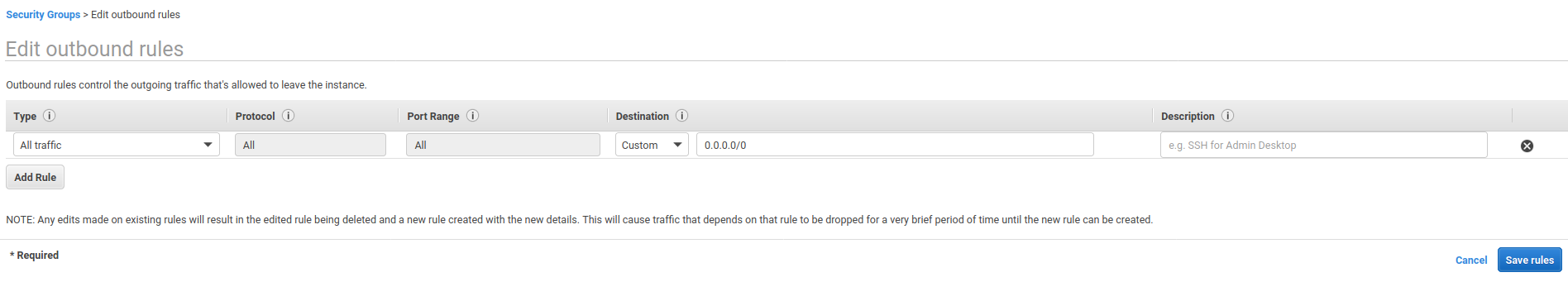
Select the Outbound Rules tab and edit the outbound rules.
Check that the outbound rules match the screenshot below. It should be configured by default.
After checking the outbound rules, create a new security group to match the below screenshot.
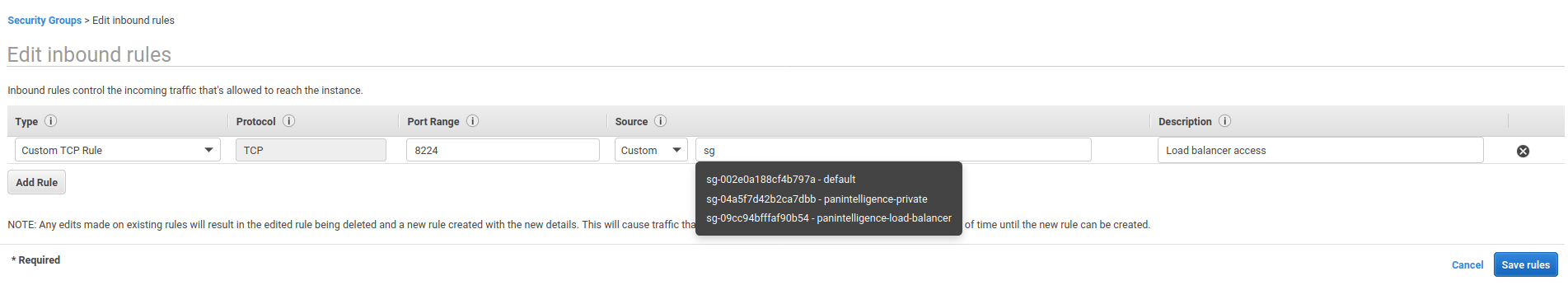
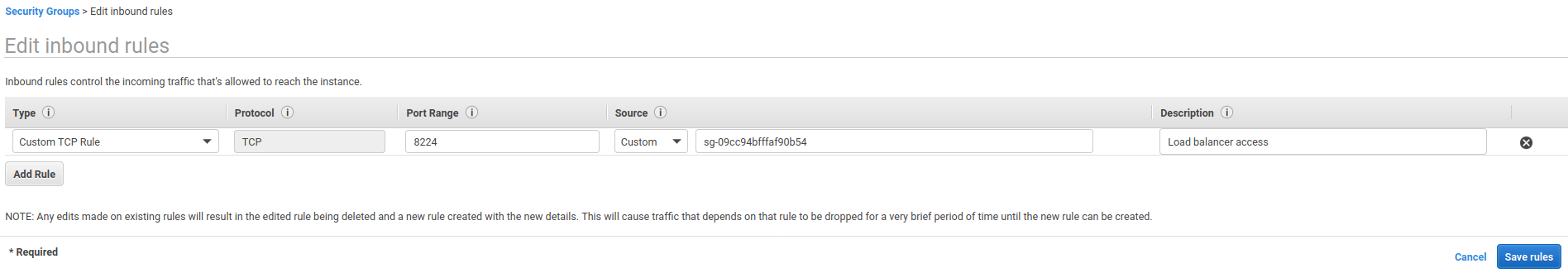
Select the created security group and select the Inbound Rules tab. Edit the inbound rules and configure it to match the screenshot below.
If you type sg in the Source input, a drop down should appear. Choose your load balancer security group you created earlier.
Check that the outbound rules match the screenshot below. It should be configured by default.
S3 Endpoint
The dashboard image includes some scripts to backup and restore the dashboard using S3.
As the dashboard server is in a private subnet, we need to create an S3 endpoint to allow the dashboard to communicate with S3.
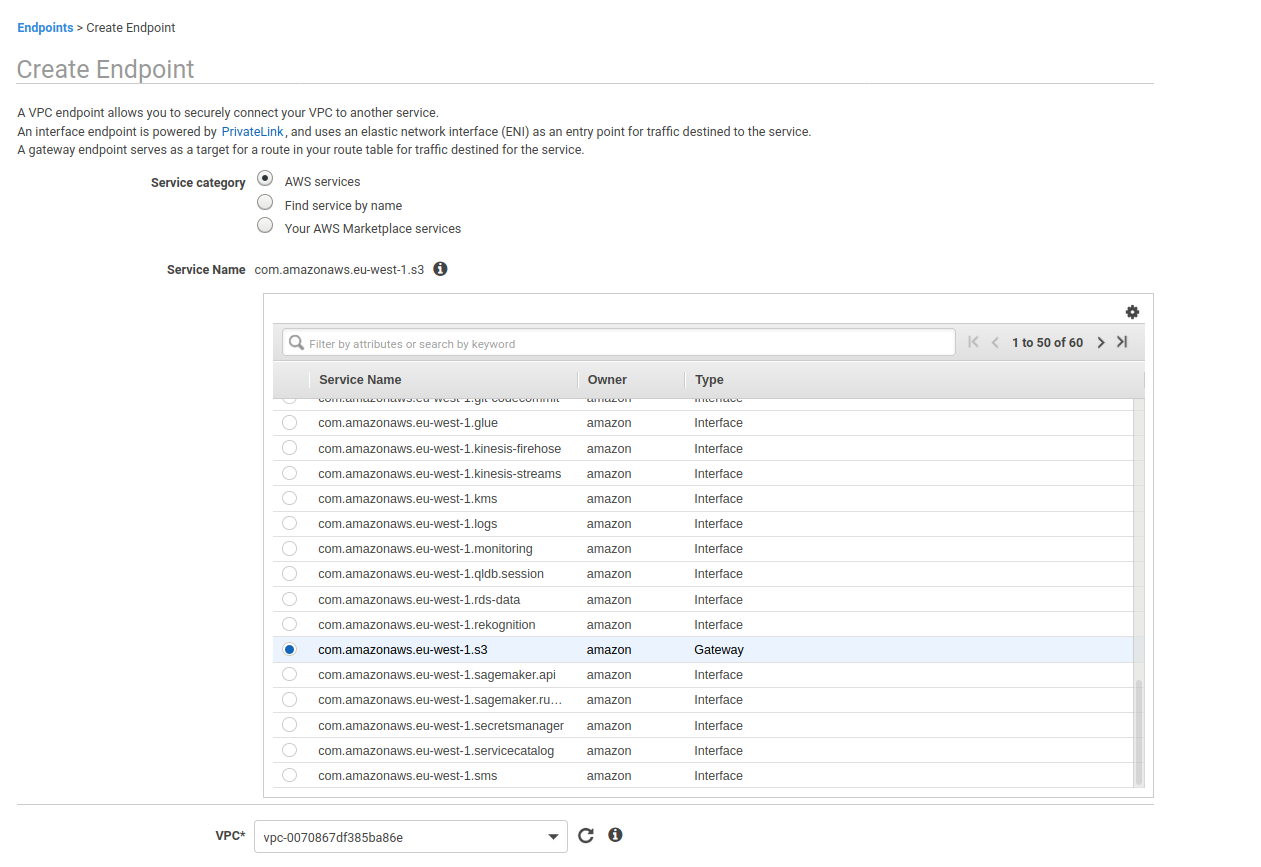
On the left of the VPC Dashboard, click the Endpoints link. From there select the Create Endpoint button.
Make sure that AWS services is selected as the Service category. For the service name, scroll to find the S3 service shown in the screenshot below.
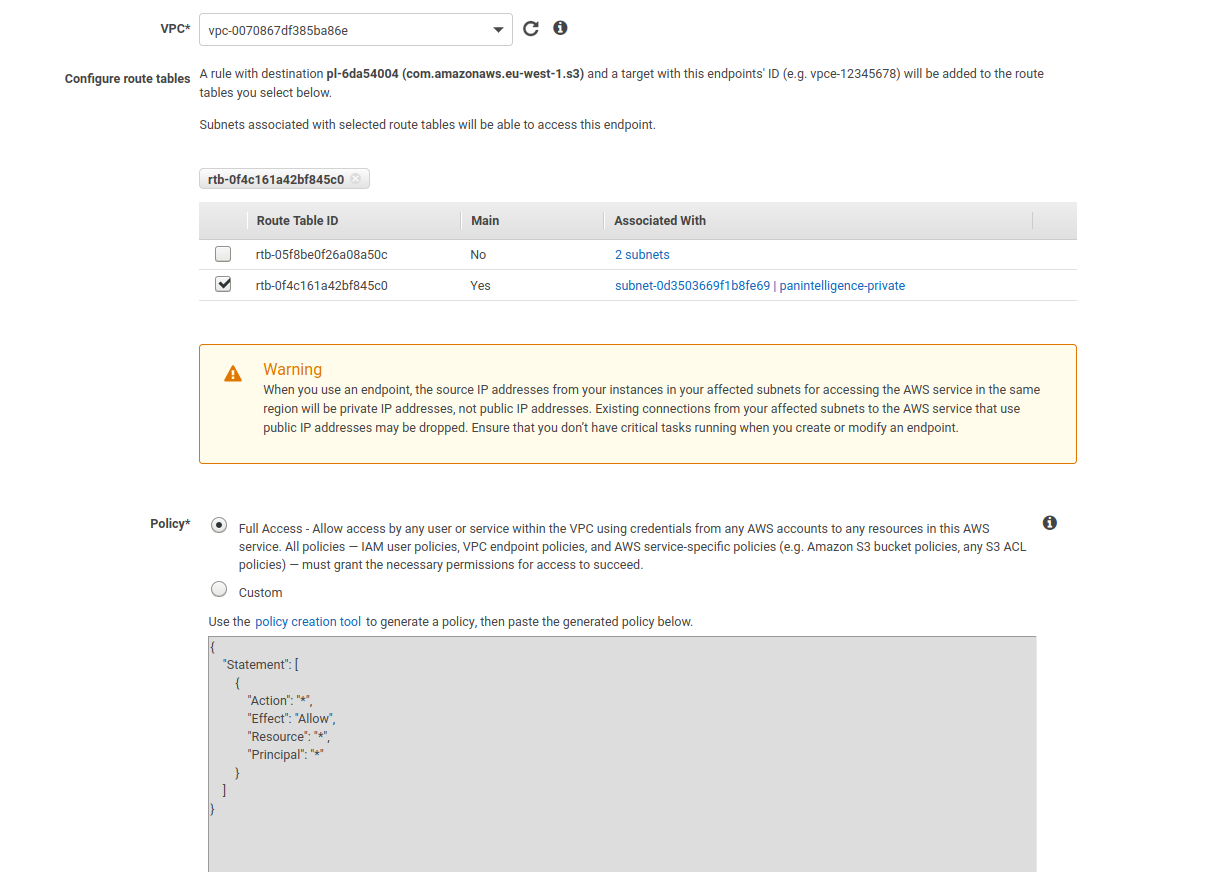
After selecting the S3 service, select the VPC you created earlier from the VPC dropdown.
Select the route table that is associated with your private subnet from the list of route tables.
You can then click Create endpoint.



0 Comments