Security Configuration
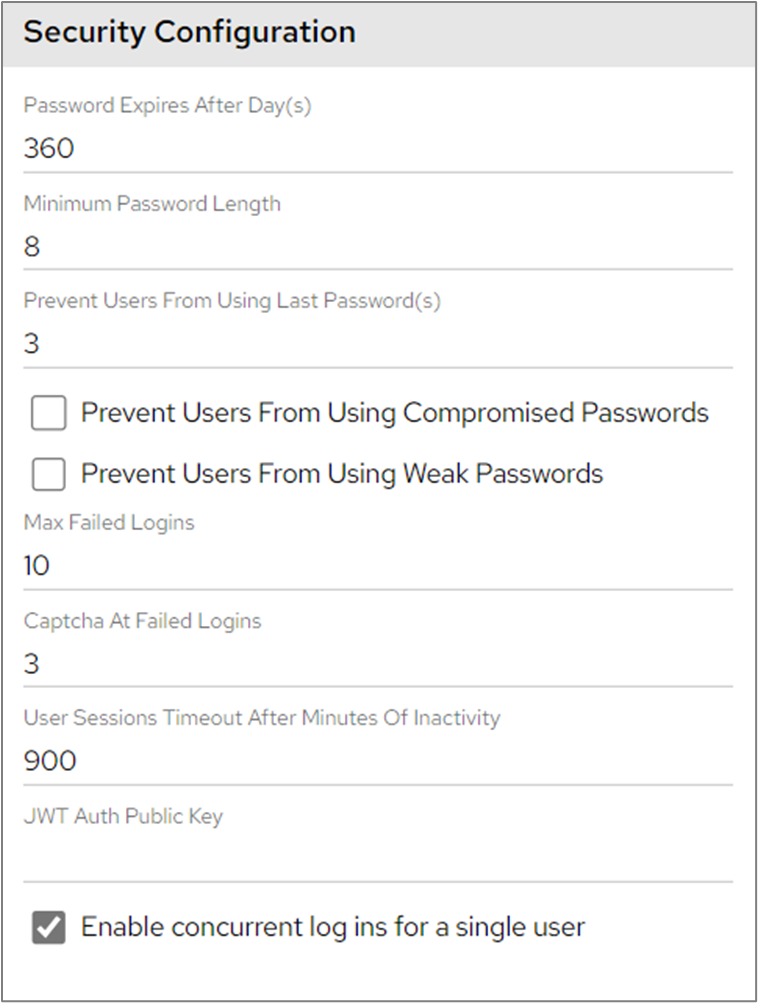
Password Expires After Day(s): The amount of time a user’s Dashboard password can remain the same before they are forced to change it.
Minimum Password Length: The minimum length that a user’s password can be set to. If a user tries to set a password shorter than this it will be rejected and they will need to set a new one.
Prevent Users From Using Last Password(s): If this is set to 15 for example, users cannot create a new password which is the same as any of their last 15 passwords.
Prevent Users From Using Compromised Passwords: This prevents the user from creating a new password which has been compromised. Compromised status is ascertained by reference to the haveibeenpwned API ( https://haveibeenpwned.com/API/v3 )
Prevent Users From Using Weak Passwords: This prevents the user from creating a new password which our password strength estimation algorithm considers ‘weak’.
Max Failed Logins: The number of times a user can attempt to log in with an incorrect username or password before their account is locked.
Captcha At Failed Logins: The number of failed login attempts by a user before a captcha image is displayed.
User Sessions Timeout After Minutes Of Inactivity: The amount of time a dashboard session will remain active if it is not being used.
JWT Auth Public Key: If you are using JWT Authentication this is where you enter (as one line, no spaces) the Base 64 String Version of your public key. See ‘Authentication’ for more information.
Enable concurrent log ins for a single user: This will allow multiple browser sessions to connect using the same piDashboard username, if the licence you are using also supports this. If this is not enabled (and/or the licence doesn’t support it) then subsequent logins will succeed, but they will automatically log out prior sessions.
Logging Settings
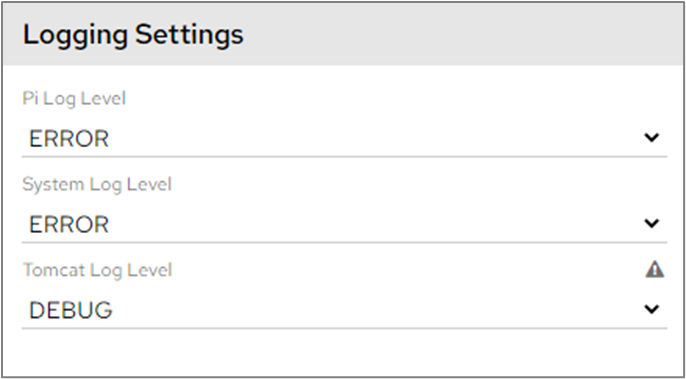
Setting the log level
Setting the log level of an application decides the amount of content to be saved to log files. It means we are interested in the current and above levels.
Severity from high to low: Fatal, Error, Warn, Info, Debug, Trace
e.g. Setting it to Warn, means
Fatal, Error, Warn logs (current and above levels) are output into log files,
Info, Debug, Trace logs (lower than this level) are ignored, these events don’t output content to log files
Error is the least granular/least verbose and debug is the most. These settings should be left to ‘Error’ unless you’re trying to investigate an issue.
Debug can very very intensive so should only be used on a temporary basis.
Log Levels and their meaning
When an application outputs logs to log files, the content is marked with a log level. The log level indicates the severity of an event.
Fatal - A log message at Fatal level indicates a system down event
Error - A log message at Error level indicates something is broken, while the system is still running (We log 500 level errors as Error)
Warn - A log message at Warn level is an unintended event that can be recovered (We log 400 level errors as Warn)
Info - Info level message captures a system event e.g. service start/stop, configuration assumptions, etc
Debug - Debug messages contain information that is diagnostically helpful, typically it has data values related to certain events
Trace - Trace level logs provide verbose content for events in a system. (We don’t log Trace level logs in our system)
Error Codes
500 level - A 500 level error is a system error, which is not recoverable from the user’s perspective
400 level - A 400 level error is a user error. The system doesn’t have any problem, and the user is doing something unintended. For example
400 - bad data is submitted, e.g. text is too long, number is too low, data format is incorrect
401 - user fails to log in, e.g. username password don’t match
403 - user is logged in but doesn’t have permission to perform a task, e.g. non-admin tries to delete a user
404 - page doesn’t exist
Network Configuration
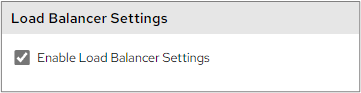
Load Balancer Settings: If you have configured load balancing (Load Balancing) and wish to utilise it click this button.
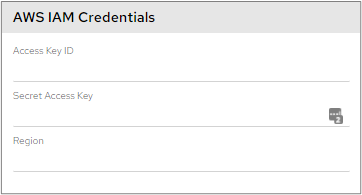
AWS IAM Credentials
Please refer to this section in our documentation on AWS Cloudformation Deployment for further information.
Server Settings
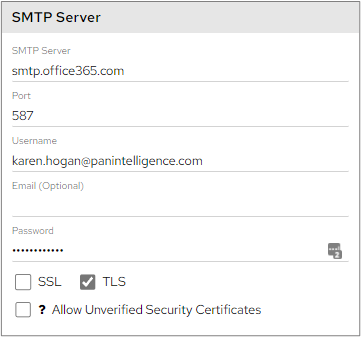
SMTP Server Instructions: for the dashboard to connect to your email server. The example shown is for Office365. SSL and TLS refer to the encryption configuration for your SMTP mail server
By default, The ‘Allow Unverified Security Certificates’ box will be unticked which will allow for the security checks to be carried out for the certificates used.
This functionality will affect the certificates used for forgotten password emails and scheduler emails.